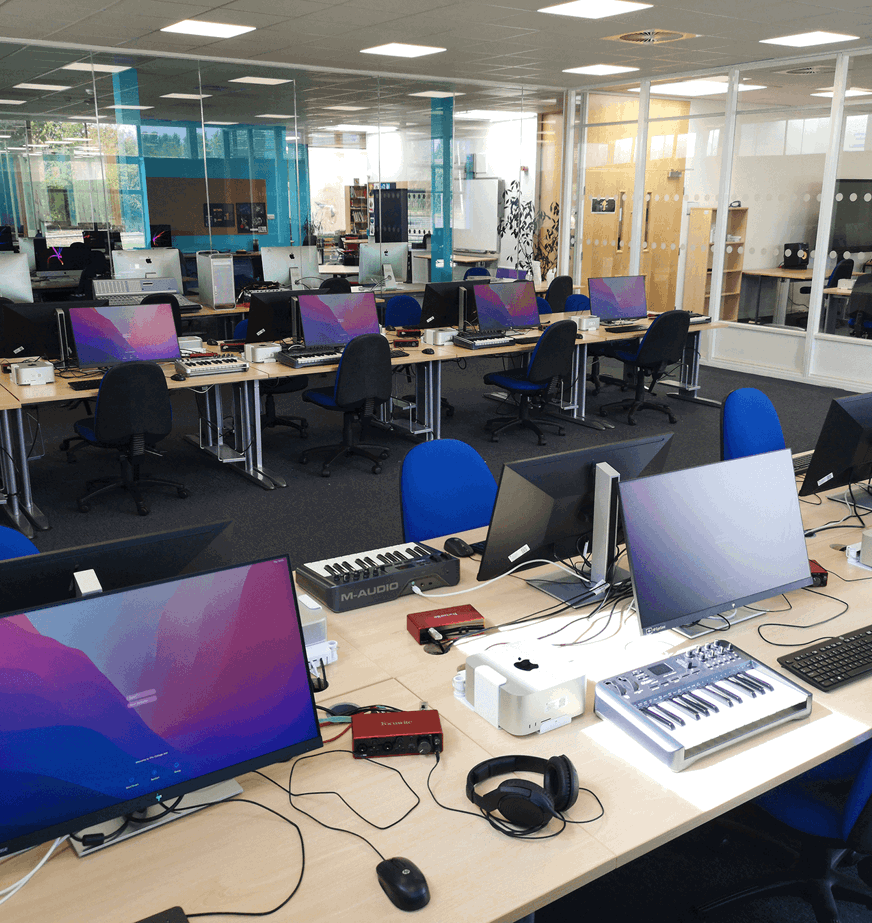
Digital, Computing and Cyber
There’s never been a better time to consider a career in Digital, Computing and Cyber, with one in ten of all Scottish job vacancies in the digital sector.
Our courses will equip you with the specialist computer science and digital media skills you need to pursue a career in areas such as software development, cyber security, 3D animation, computer games design, digital design and eSports.

Why choose Digital, Computing and Cyber
Strong digital and cyber skills can lead to many exciting job opportunities, not only in IT businesses but across all sectors including banking and finance, creative industries, education, engineering, tourism, healthcare and the public sector.
The average salary for digital technology professionals is higher than the average Scottish salary and is continuing to grow.
We’ve recently invested hugely in our digital infrastructure, creating the highest quality learning environment with access to the latest software and intrusion detection systems, giving you the edge over other similarly-qualified applicants when you enter the job market.
Our courses can lead to careers in areas such as games development, cyber security, software development, mobile app development and web development.
What we offer
- Cyber Security
- Games Development and Design
- 3D Computer Animation
- eSports
- Digital Design
- Web Development
- Software Development
Progress to a degree
Did you know that our HNC and HND Digital, Computing and Cyber courses are the equivalent of the first and second years of a degree?
Depending on the subject you study, successfully completing an HNC or HND in Digital, Computing and Cyber courses at Fife College could mean you have the opportunity to progress to years 2 or 3 of a related BSc or BSc (Hons) degree course at one of our partner universities.
Studying Digital, Computing and Cyber at Fife College can be a more cost-effective, local alternative route to the same degree in Scotland, in the same amount of time!
Find out more about degree pathways.
Derek Martin-Stead
HND Software Development
"The overall experience at Fife College for me has been exceptional. The atmosphere here is fantastic."